Wifite is a tool to audit WEP or WPA encrypted wireless networks. It uses aircrack-ng, pyrit, reaver, tshark tools to perform the audit. This tool is customizable to be automated with only a few arguments and can be trusted to run without supervision. Sep 04, 2018 Wifite 2. A complete re-write of wifite, a Python script for auditing wireless networks. Cleaner process management. Does not leave processes running in the background (the old wifite was bad about this). Where does wifite save handshakes? If this is your first visit, be sure to check out the FAQ by clicking the link above. You may have to register before you can post: click the register link above to proceed.
Disclaimer: What you do with this information is up to you. You are fully responsible for what you do with this info, and how you use it. HackMethod is not responsible for your actions. Please do not hack Wifi points that you are not allowed to.
NOTE: I do advise having a USB WiFi adapter, and an extra point would be to get a great one like the ALFA AWUS036NHR or AWUS051NH. Although any card would do as long as it supports monitor mode and packet injection.
Introduction
When it comes to the world of WiFi hacking, the possibilities are only limited by your imagination. Skilled hackers can combine attacks together for increased efficiency, and can also judge on which attack is best to use given a particular situation. By the end of this guide you should have an overall idea on the types of attacks that you can use against any WiFi-enabled AP or router.
Getting Started
The tool that this guide will be using is Wifite.
Now I wont be including how to do it using any other tools, because this should work just fine. I’ll leave the exploration up to you.
To get started, install Wifite on your machine by following the installation instructions that are stated here.
Scanning for Wifi points
Simply run wifite.py -i <wlan interface here *NOT IN MONITOR MODE*> or if you didnt understand the previous command simply use wifite.py and it will begin scanning for nearby access points and their features (Encryption method and if WPS is enabled or not).
NOTE: I always recommend to spoof your mac address using the --mac flag to the program or macchanger. Its for your safety.

Here are the 3 types of targets you can find:
- WEP protected routers
- WPA/WPA2 protected routers
- Open routers
Now within those categories, you can find a feature called WPS (Wi-Fi Protected Setup) enabled, which uses an 8 digit PIN to add devices to a WiFi network without having to input long passwords.
Wifi Telephone
Attacking WEP protected WiFi points
WEP is an old and depreceated way of protecting WiFi passwords, so if you find one, you are in luck. WEP takes substantially less time. This is easily automated in Wifite, and it even uses multiple attacks against routers to get the password. You only need around ~10 to 120 minutes to crack WEP, maybe longer. I cant say much because I have never seen any WEP protected routers were I live and never had the time to set one up and try myself.
Here is how the attack should look (picture taken from Wifite Github wiki):
Attacking WPA/WPA2 protected WiFi points
When it comes to WPA, we need to grab the handshake by deauthing clients who are connected to the router and sniffing the handshake as it goes. This is automated in Wifite, and it handles everything. Note: You may grab the handshake in a small amount of time, but cracking the hash itself will take a pure brute-force attack or a wordlist, which takes alot of time. Only use this method if you have a really powerful GPU/CPU or if all other options have failed.
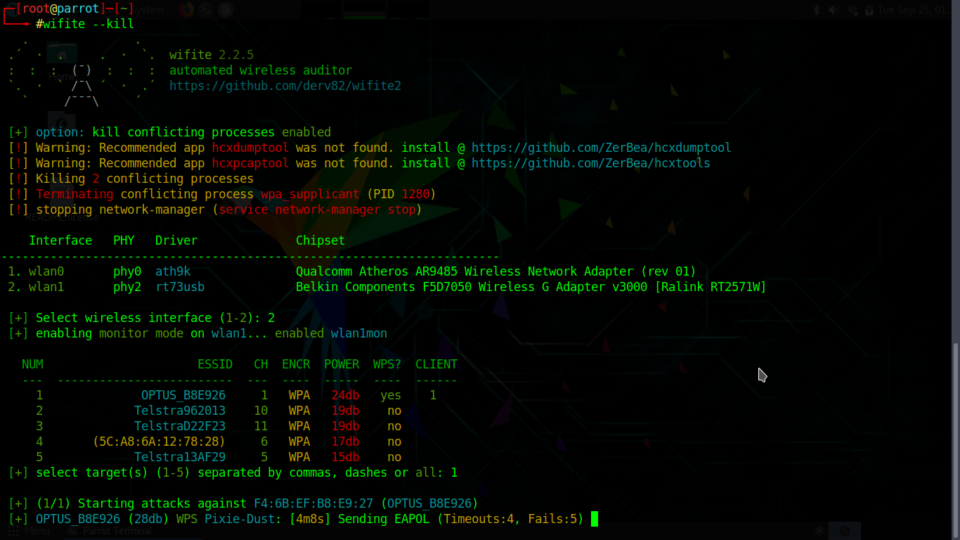
Attacking WPS enabled WiFi points
Now comes the fun part, WPS cracking. There are 2 attacks you can do on WPS enabled routers, a WPS PIN bruteforce and a WPSPixie attack. The WPS PIN attack works online, as in all PIN guesses are actually sent to the router, while the WPSPixie attack works offline and without flooding the router with WPS PIN attempts.
Now the obvious disadvantage about the WPS PIN attack is that some routers have on-board anti-bruteforce mechanisms and will stop accepting your attempts after a few attempts. I only go this route if the WPSPixie attack fails and there is no anti-bruteforce mechanism (Wifite will tell you if detects one).
The WPSPixie attack is one of the best attacks on Wifi points I have ever seen. In most cases, you can get the WiFi password in minutes or even a few seconds. Be aware that it may take up to 30 minutes in some cases, although I have never personally seen it go beyond 10 or so minutes. NOTE: The WPSPixie attack may not work on some routers, and you will have to choose a different route. (Wifite will also notify you if the WPSPixie attack will not work.
NOTE: Sometimes you will see that Wifite gets stuck at Waiting for beacon from 'xx:xx:xx:xx'. If it gets stuck for a while at this point, press CTRL+C and move on to a different target.
Contoh rab rumah 50 juta. Wifite hacking WPS enabled points using WPS PIN Bruteforce
Conclusion
Bloons monkey city hacked apk free download. So thats pretty much it when it comes to hacking WiFi using Wifite. There are other ways of doing this, such as using the aircrack-ng suite of tools and/or using dedicated WPS hacking tools such as reaver. Additionally, this guide is only but a small slice of the world of wireless hacking, so be sure to stay tuned for more wireless hacking tutorials soon!
WiFite Description
Wifi Tester
To attack multiple WEP, WPA, and WPS encrypted networks in a row. This tool is customizable to be automated with only a few arguments. Wifite aims to be the 'set it and forget it' wireless auditing tool.

Features
- sorts targets by signal strength (in dB); cracks closest access points first
- automatically de-authenticates clients of hidden networks to reveal SSIDs
- numerous filters to specify exactly what to attack (wep/wpa/both, above certain signal strengths, channels, etc)
- customizable settings (timeouts, packets/sec, etc)
- 'anonymous' feature; changes MAC to a random address before attacking, then changes back when attacks are complete
- all captured WPA handshakes are backed up to wifite.py's current directory
- smart WPA de-authentication; cycles between all clients and broadcast deauths
- stop any attack with Ctrl+C, with options to continue, move onto next target, skip to cracking, or exit
- displays session summary at exit; shows any cracked keys
- all passwords saved to cracked.txt
- built-in updater: ./wifite.py -upgrade
Homepage: https://github.com/derv82/wifite2
Author: derv merkler
License: GPLv2 Best software to extract subtitle from dvd.
WiFite Help
WiFite Usage Example
Attack access points with over 50 dB of power (-pow 50) using the WPS attack (-wps):
How to install WiFite
The program is pre-installed on Kali Linux.
Wifite Kali
Installation on Linux (Debian, Mint, Ubuntu)
Required Programs
Please see the installation guide on the wiki for help installing any of the tools below.
- Python 2.7.x. Wifite is a Python script and requires Python to run.
- aircrack-ng suite. This is absolutely required. The specific programs used in the suite are:
airodump-ng
packetforge-ng
Standard linux programs.
- iwconfig, ifconfig, which, iw
Suggested Programs
- reaver, a Wifi-Protected Setup (WPS) attack tool. Reaver includes a scanner 'walsh' (or 'wash') for detecting WPS-enabled access points. Wifite uses Reaver to scan for and attack WPS-enabled routers.
- pyrit, a GPU cracker for WPA PSK keys. Wifite uses pyrit (if found) to detect handshakes. In the future, Wifite may include an option to crack WPA handshakes via pyrit.
- tshark. Comes bundled with Wireshark, packet sniffing software.
- cowpatty, a WPA PSK key cracker. Wifite uses cowpatty (if found) to detect handshakes.


WiFite Screenshots
WiFite Tutorials
Related tools
- Penetrator-WPS (76.8%)
- Router Scan (75%)
- OneShot (74.3%)
- Fern Wifi Cracker (73.2%)
- airgeddon (70.7%)
- Wash (RANDOM - 56.7%)